Virtual Network Functions in VPC and Integration With Event Notifications in IBM Cloud
Explore Virtual Network Functions (VNFs) for VPC in IBM Cloud, VNF High Availability solutions, standalone and HA VNF installation, and its integration.
Join the DZone community and get the full member experience.
Join For FreeWhat Are Virtual Network Functions (VNFs)?
Previously, proprietary hardware performed functions like routers, firewalls, load balancers, etc. In IBM Cloud, we have proprietary hardware like the FortiGate firewall that resides inside IBM Cloud data centers today. These hardware functions are packaged as virtual machine images in a VNF.
VNFs are virtualized network services that are packaged as virtual machines (VMs) on commodity hardware. It allows service providers to run their networks on standard servers instead of proprietary ones. Some of the common VNFs include virtualized routers, firewalls, load balancers, WAN optimization, security, and other edge services. In a cloud service provider like IBM, a user can spin up these VNF images in a standard virtual server instead of proprietary hardware.
What Is Network Function Virtualization (NFV)?
NFV is a technology that allows network operators to virtualize network functions and services and run them on commodity hardware. The NFV Orchestrator (NFVO) is responsible for the life cycle of VNF. In NFV, VNFs are instantiated, managed, scaled up or down, and terminated, when no longer required.
How NFV Works in IBM Cloud
The NFV solution internally uses the IBM Cloud Schematics service, which is a wrapper over the Infrastructure As Code (IaC) tool, Terraform, to provision resources in Cloud. Terraform takes care of creating, updating, and deleting the VNF Instances in Cloud. IBM Cloud VNF vendors like F5, Check Point, and Palo Alto will onboard their images (qcow2 images) to IBM Cloud. In VPC, these images are available as custom images. Vendors provide a public GitHub repository that contains Terraform code for provisioning their VNF instance in IBM Cloud. Finally, the VNF vendor will publish their service in the IBM Content Catalog. Whenever a user tries to create a VNF service in IBM Content Catalog, internally it will create a VNF Instance through Terraform code provided by the vendor. This is the F5 image that is available in the IBM Cloud Catalog.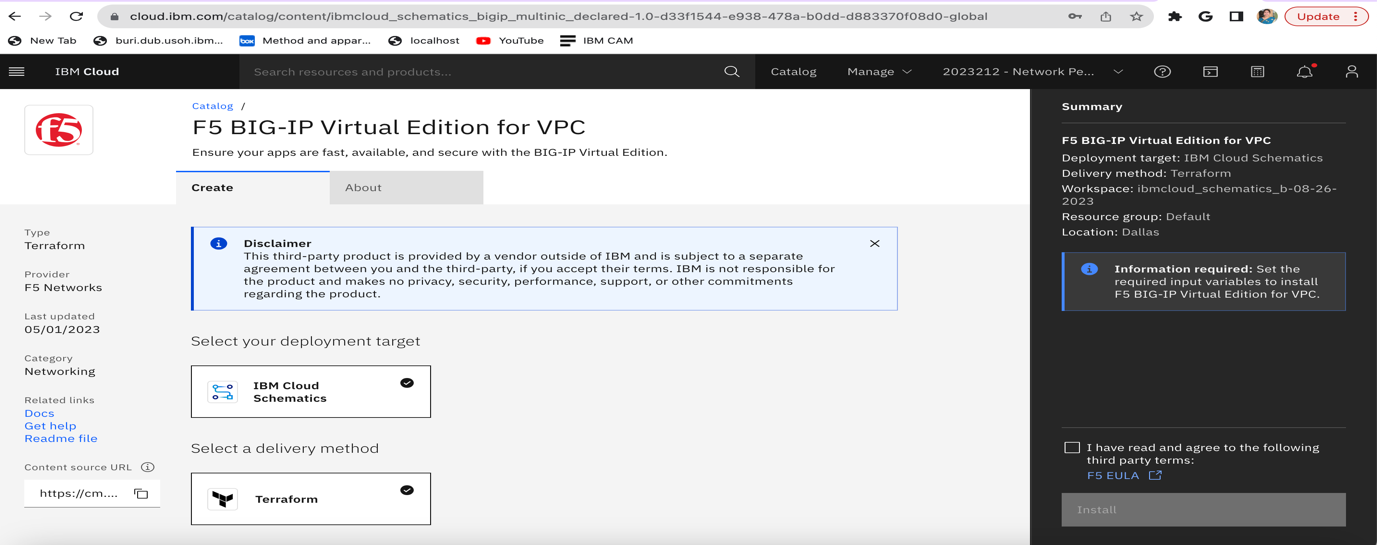 IBM Cloud VPC customers want to have a VNF firewall in front of their traffic so that a VNF firewall appliance will control traffic and filter any bad traffic. This is to provide security to their VPC customers. Also, VPC customers want to install VNF in High Availability (HA) mode. A single VNF may cause an outage when the VNF goes down. In HA mode, if one of the VNF goes down, then the other VNF will take over the control. IBM Cloud customers like BNPP use F5 load balancers.
IBM Cloud VPC customers want to have a VNF firewall in front of their traffic so that a VNF firewall appliance will control traffic and filter any bad traffic. This is to provide security to their VPC customers. Also, VPC customers want to install VNF in High Availability (HA) mode. A single VNF may cause an outage when the VNF goes down. In HA mode, if one of the VNF goes down, then the other VNF will take over the control. IBM Cloud customers like BNPP use F5 load balancers.
VNF High Availability
There are two types of High Availability in VNF:
Active-Active Mode
In active-active mode, both of the VNFs are active. Between the two VNFs, there is a load balancer that connects traffic. The load balancer will route the traffic in a round-robin fashion to one of the VNFs.
Active-Passive Mode
In active-passive mode, one of the VNFs is active and the other VNF (in passive mode) will act as a backup in the event of an outage. Based on the health check of the active VNF, the active-passive state of the VNFs is swapped and the traffic will failover to the currently active VNF. There is an application that will change the ingress or egress routes with the next hop IP address of the currently active VNF using the VPC Rest API. Currently, FortiGate is the only customer who does that in IBM Cloud.
Customers prefer active-passive VNF HA as it is more cost-effective when compared to active-active VNF HA. Usually in any networking device like the VNF, there are 2 costs:
- Unmetered: Device running cost
- Metered: Data/traffic cost
In the case of metered, the cost doesn’t vary, whether it is active-passive or active-active. But in the case of unmetered, there is some difference. The difference is that a standby device will always consume less power compared to an active device due to the reasons below:
- In standby devices, it has 3 interfaces: internal, external, and HA. However, when it is in standby mode, only its HA interface is being used for data sync from active devices whereas the other 2 interfaces are idle. This is not the case of an active device, where all 3 interfaces are used.
- Due to some minimal tasks running in the standby device, fewer resources like CPU and RAM are being utilized, and the power consumption and hence, the cost of running a standby device will be less compared to an active device.
Active-Active VNF Solution in VPC
Please refer to the "Active/Active HA transparent VNF (single, multi-zone region VPC)" documentation, Use Case 2.
Active-Passive Solution in VPC
Here is a sample application that a VNF Vendor like F5 or Palo Alto can refer to to change the ingress or egress routes with the next hop IP address of the currently active VNF using VPC Rest API. The application has the following features:
- It can be run as an IBM Kubernetes Service (IKS) and code engine-based VNF HA application that will change the VPC custom routes with the next hop as the currently active VNF.
- The application accesses VPC SDK for changing custom routes using the management subnet that is attached to the Public Gateway.
- The application is private, scalable, and highly available.
The figure below illustrates an active-passive Virtual Network Function (VNF) HA Solution that is running in IKS or Code Engine. This link can provide more information on how to install the HA solution in the F5 VNF HA setup. The GitHub repository also has instructions to install the VNF as a standalone and in High Availability mode. F5 and Palo Alto VNFs have failover-detecting mechanisms that can be used to trigger failover scripts. The HA application works well in both IBM Kubernetes Service and IBM Cloud Code Engine. In IBM Cloud, the custom route table is zone-specific, so it cannot be used in cross-zone VNF HA setup. The VNFs in HA should be in the same zone only for the HA solution.
This link can provide more information on how to install the HA solution in the F5 VNF HA setup. The GitHub repository also has instructions to install the VNF as a standalone and in High Availability mode. F5 and Palo Alto VNFs have failover-detecting mechanisms that can be used to trigger failover scripts. The HA application works well in both IBM Kubernetes Service and IBM Cloud Code Engine. In IBM Cloud, the custom route table is zone-specific, so it cannot be used in cross-zone VNF HA setup. The VNFs in HA should be in the same zone only for the HA solution.
Here is the VPC Routing Table with the next hop of the currently active VNF: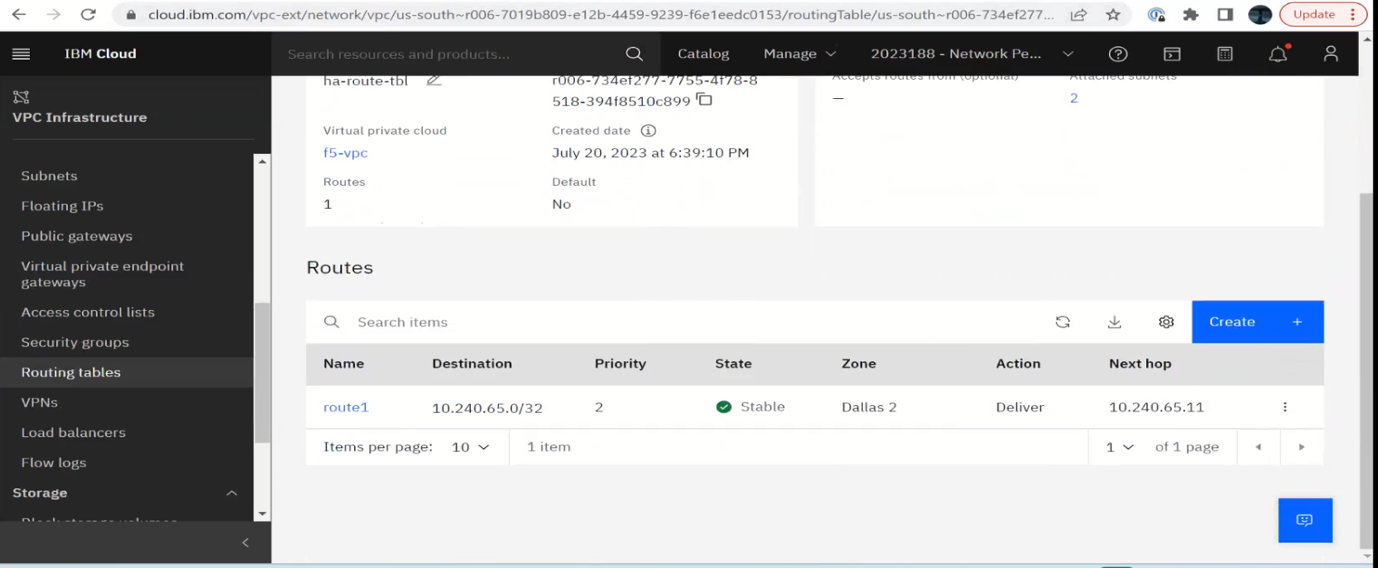
F5 VNF Active-Passive HA
The failover script is found under the directory /config/failover/tgactive in an Active/Passive F5 instance. The failover script invokes the IKS or Code Engine application to update the next hop IP to all of the ingress or egress routes in the VPC routing table. The VNF HA setup is private and cannot access the internet for security reasons; hence, use the management subnet for accessing the HA application, as shown below:
curl --interface mgmt http://063af6bc-us-south.lb.appdomain.cloud:8000/f5/failover
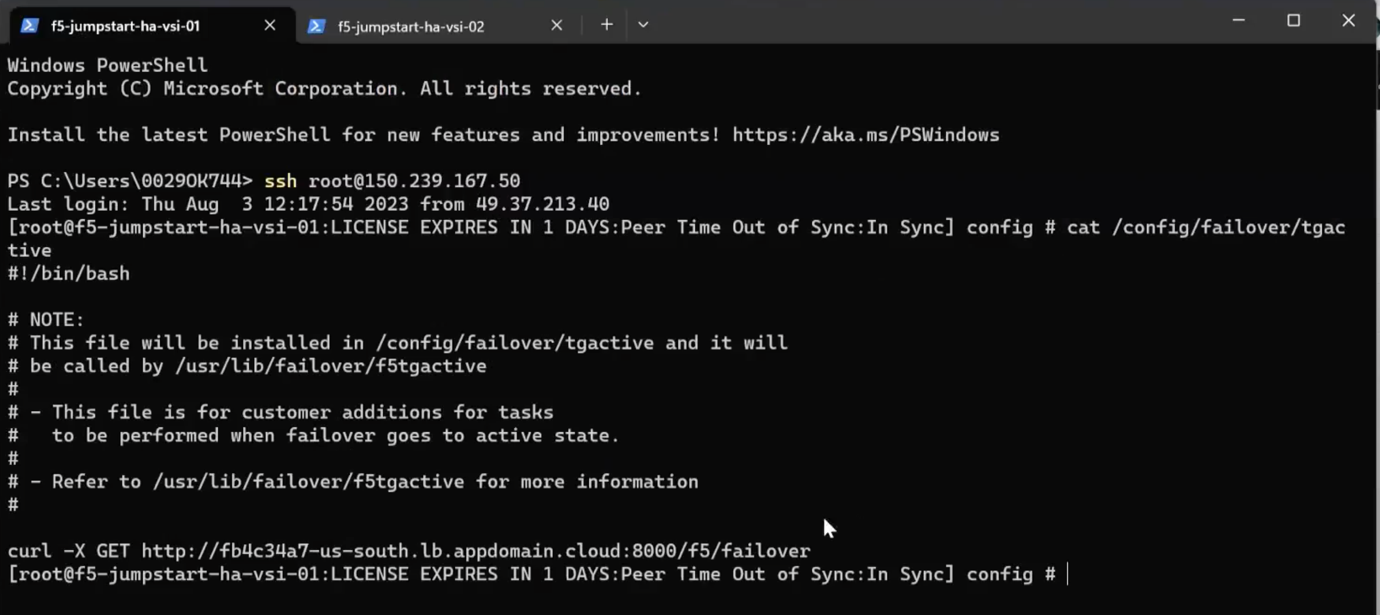
In the failover script, you can add a notification to send an email to the admin or an operator. The operator can check the issue in VNF which went down and bring it up.
VNF Integration With IBM Event Notification
In the context of a failover script, the incorporation of IBM Cloud Event Notifications with the Custom Email Destination feature provides a valuable tool for improving the response to issues in a VNF (Virtual Network Function). Here's how it can work:
- When a VNF goes down or encounters an issue, the failover script can be configured to trigger an automatic notification. This notification can be sent as an email to the designated admin or operator responsible for managing the VNF.
- The operator, upon receiving the email notification, can promptly investigate the issue with the VNF that went down. With timely information at their fingertips, they can take the necessary steps to bring the VNF up and resolve the issue efficiently.
By using the Custom Email Destination feature in IBM Cloud Event Notifications, businesses can extend the capabilities of their failover scripts and enhance their incident response procedures. This approach aligns with the broader theme of leveraging technology to optimize operations and improve customer satisfaction, as discussed in the previous example.
- Example request for sending notifications:
curl -X POST — location — header "Authorization: Bearer {iam_token}" — header "Content-Type: application/json" "{base_url}/v1/instances/{instance_id}/notifications"- Example JSON body for sending notifications to various destinations:
{
"id":"b2198eb8-04b1-48ec-a78c-ee87694dd845",
"time":"06/06/2022, 14:23:01",
"type":"com.ibm.cloud.sysdig-monitor.alert:downtime",
"message_text":"Hi, Welcome from the IBM Cloud - Event Notifications service!",
"source":"apisource/git",
"specversion":"1.0",
"ibmensourceid":"d6f08a53-05f6-465f-903e-03db3fa91b64:api",
"data":{
"greet":"Afternoon",
"create_time":"2022-07-06T09:19:45.213429645Z",
"create_timestamp":1657099185,
"issuer":"IBM Cloud VNC",
"issuer_url":"https://cloud.ibm.com/vnc, ""long_description"": ""Success! Your Event Notifications instance is configured with IBM Cloud VNC"", ""payload_type"": ""test"", ""reported_by"": { ""id"": ""compliance"", ""title"": ""IBM Cloud VNC"", ""url"": ""https":" }, ""severity"": ""LOW"", ""short_description"": ""Success! Your Event Notifications instance is configured with IBM Cloud VNC."", ""transaction_id"": "e539778e-4915-4586-b4c9-48e44af5c010", ""name"": ""IBM Cloud Event Notifications"", ""price"": "100", ""rating"": "4.9" }, ""datacontenttype"": ""application/json"", ""ibmendefaultlong"": ""This is a original long message"", ""ibmendefaultshort"": ""IBM Cloud Event Notifications is a routing service that provides information about critical events in your IBM Cloud account"", ""ibmenfcmbody"": "{
"\\""notification\":{\"title\":\"Hello Pradeep, Your Order summary - Hot Chilli Manchurian ($20) and French Fries ($11) is on its way!\",\"time_to_live\":100}}",
"ibmenpushto":"{\"platforms\":[\"push_chrome\"]}",
"ibmenmailto":"[\"pgopalgo@in.ibm.com\"]",
"personalization":{
"pgopalgo@in.ibm.com":{
"name":"Pradeep"
}
}In summary, Integrating IBM Cloud Event Notifications with Custom Email Destination in failover scripts enhances operational efficiency and allows for a swift response to VNF issues, minimizes downtime and potential disruptions to services, ultimately benefiting both the business and its customers by ensuring uninterrupted services. It empowers operators with real-time alerts, enabling them to take proactive measures to maintain the stability and reliability of the network. Furthermore, customers have the flexibility to choose from a range of notification options, including PD (PagerDuty), SMS, Slack, and more in addition to custom email notifications, ensuring they receive alerts in the manner that best suits their needs and preferences.
For more detailed information on implementing such notifications and utilizing IBM Cloud Event Notifications for VNF integration, you can refer to the provided documentation and example request.
Palo Alto VNF Active-Passive HA
The GitHub repository has instructions to install the VNF as a standalone and in High Availability mode. The active-passive HA application works in IBM Kubernetes Service and Code Engine. The figure below shows Palo Alto VNF HA running in active-passive mode.
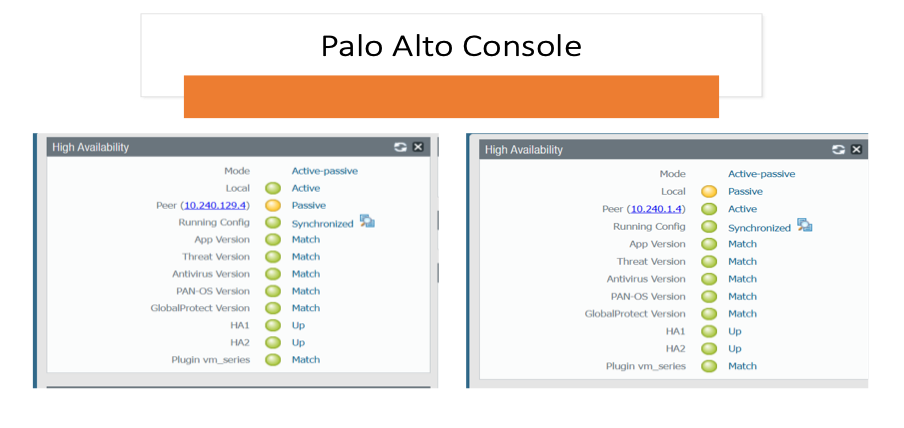
Check Point VNF Active-Active HA
The figure below illustrates an active-active Virtual Network Function (VNF) HA Solution that runs with Network Load Balancer.
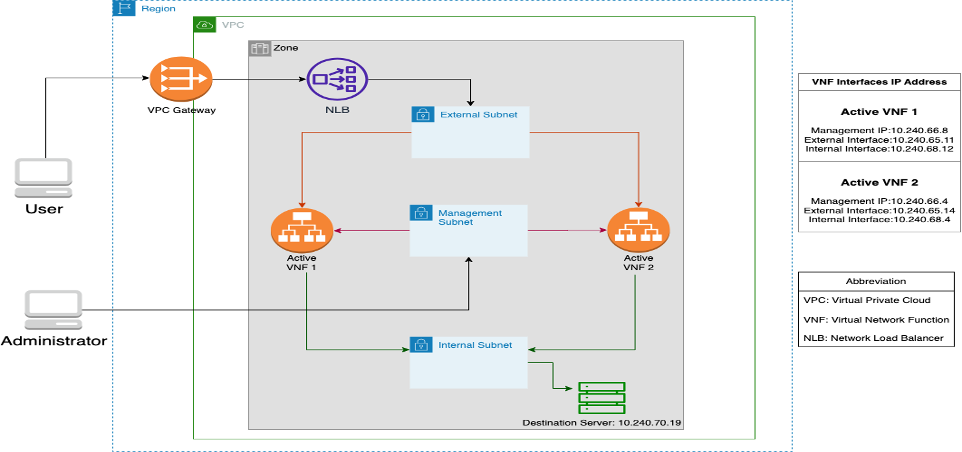
This GitHub repository has instructions to install the VNF as a standalone and in High Availability mode. The HA application works only in active-active mode. The figure below shows Check Point VNF HA running in active-active mode.
Here is the screenshot of the active-active VNFs cluster state:

Conclusion
You now have a basic understanding of how VNF works in IBM Cloud. You also saw the different VNF High Availability solutions available in VPC. You can install VNF in standalone and High Availability mode by following the instructions specified in the public GitHub repository found in this blog.
You can find these NFVs in the IBM Cloud Catalog:
Opinions expressed by DZone contributors are their own.

Comments